I've compiled using PlatformIO.
I noticed problems when using FlasherX that it wouldn't move the data. Turns out that EHEX has two EOF's for some strange reason.
At the end we have the regular EOF but about 200 lines further up there is another EOF. This confuses FlasherX.
Should it really be like this?
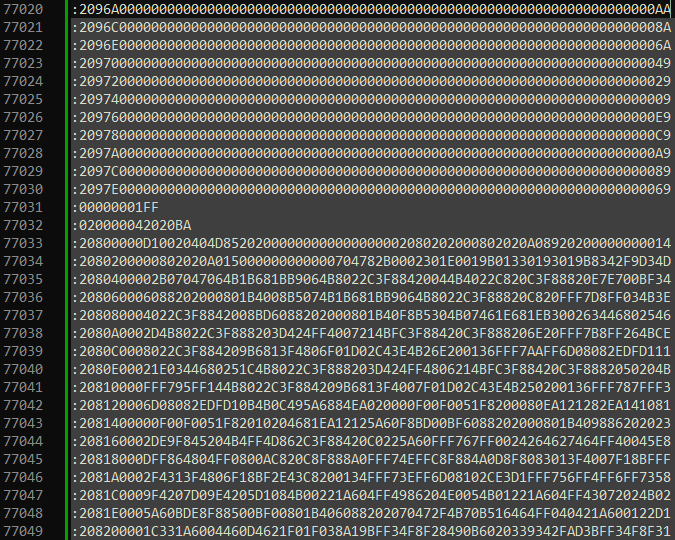
I noticed problems when using FlasherX that it wouldn't move the data. Turns out that EHEX has two EOF's for some strange reason.
At the end we have the regular EOF but about 200 lines further up there is another EOF. This confuses FlasherX.
Should it really be like this?

